For Sigma organizations running on Microsoft Azure (Azure), secure connection to your data using Azure Private Link is supported. Azure Private Link is a security feature available for Azure accounts. It will allows connections between your Azure Virtual Network (VNet) and other services, without sending traffic over the public internet.
In this case, the Secure Link will be created between Sigma and your data warehouse, all inside Azure.
The Azure private link service enables Sigma, which runs in a isolated private virtual network in Azure, to reach customer data via Azure's internal network such that no traffic is transmitted over the public internet.
Azure Private Link provides enhanced security, reduced network latency, simplified networking, cost-effectiveness, and compliance with regulations.
Sigma currently supports creating private links to three kinds of data warehouse that runs in Azure; Snowflake, Databricks and Postgesql.
Please check here for the latest information on supported connections
Standing up a Private Link requires a customer's cloud administrator (or similar role) to provide specific configuration detail to Sigma so that the Private Link connection can be established. This is covered in each section later and depends on data warehouse type.
The process of creating the Private Link can take 2-3 business days once the request is acknowledged by Sigma.
For more information on Sigma's product release strategy, see Sigma product releases.
Target Audience
Administrators who require secure, private connections between Sigma and data in a warehouse.
Prerequisites
- A computer with a current browser. It does not matter which browser you want to use.
- Access to your Sigma environment. A Sigma trial environment is not supported for Private Link.
- Some familiarity with Sigma is assumed. Not all steps will be shown as the basics are assumed to be understood.
- Administrative access to the data warehouse private link connects to.
- A Microsoft Azure account with Administrative access.
What You'll Learn
How to establish a secure connection between Sigma and an Azure data warehouse.
Azure Private Link provides private connectivity to Snowflake by ensuring that access to Snowflake is through a private IP address.
Azure Private Link is not a service provided by Snowflake. It is a Microsoft service that Snowflake enables for use with your Snowflake account.
Once provisioned, traffic will only occur between Sigma and Snowflake using the Microsoft backbone to avoid the public Internet.
This keeps access rules private while providing secure and private communication.
Provide Snowflake Info to Sigma
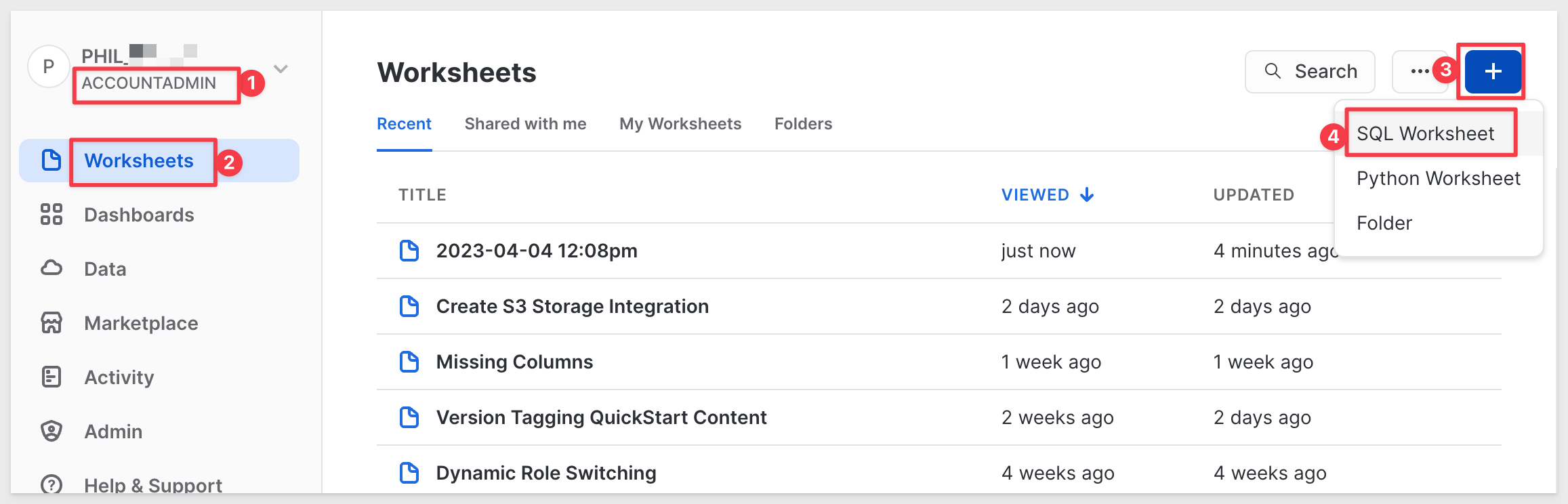
Begin by logging into Snowflake as ACCOUNTADMIN and clicking the + to create a new Worksheet and select SQL Worksheet:
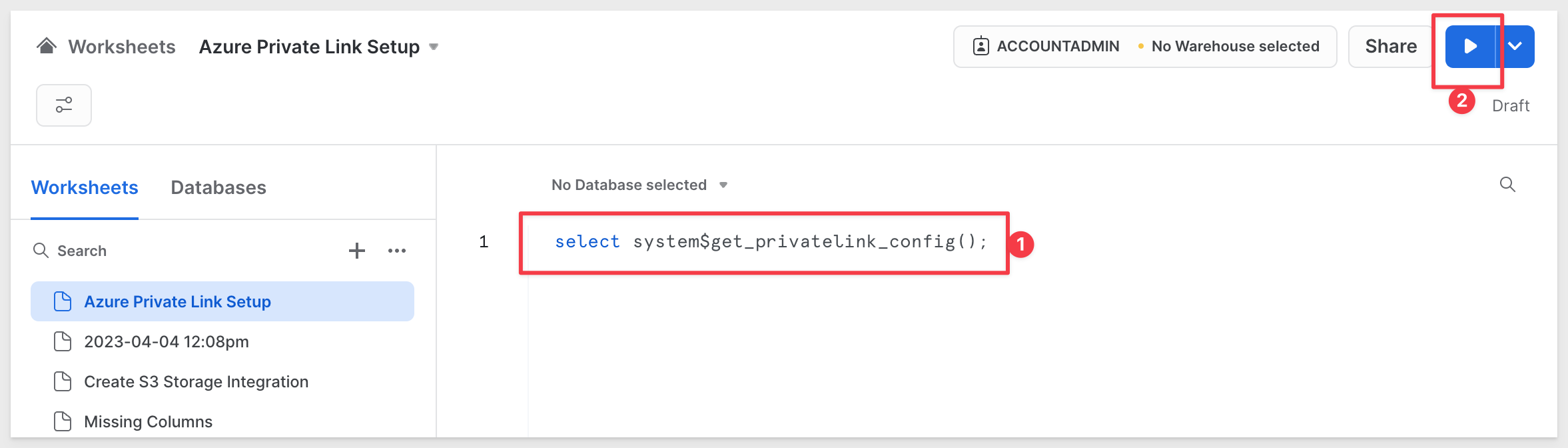
Copy and paste the following command and run it
select system$get_privatelink_config();
Below is the output from the SQL query. In the example above, the required output is highlighted:
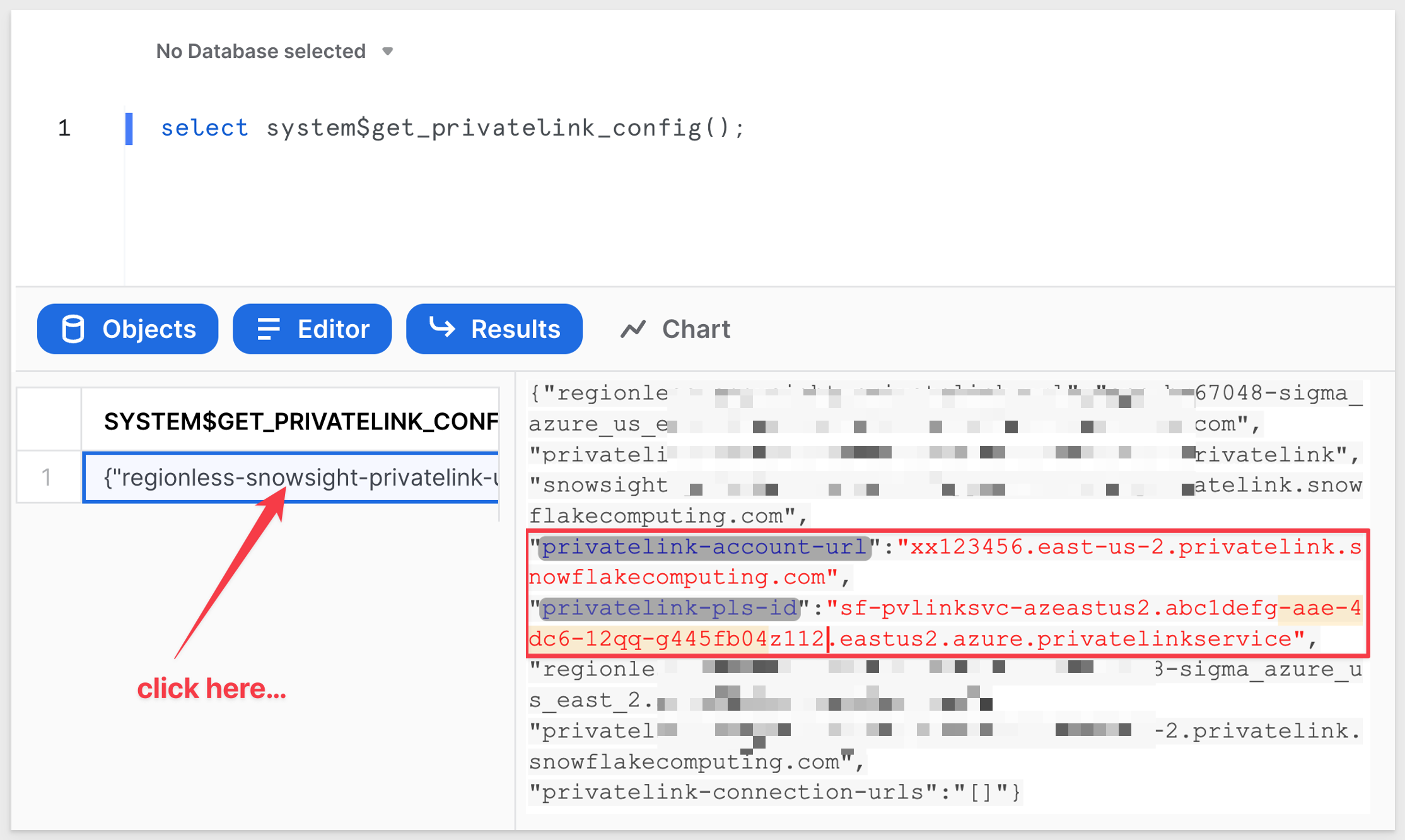
In the example above, private-pls-id is:
xx123456.east-us-2.privatelink.snowflakecomputing.com
and the privatelink_ocsp-url is:
sf-pvlinksvc-azeastus2.abc1defg-aae-4dc6-12qq-g445fb04z112.eastus2.azure.privatelinkservice
Copy the values generated for your Snowflake account and send these to your Sigma account manager.
Sigma will create a Private Link and alert you when the link is active.
Once you receive notification from Sigma (in email) you can create the new connection in Sigma.
Configure Snowflake Connection
In Sigma go to Admin > Connections > Snowflake.
Click Create to create a Snowflake connection:
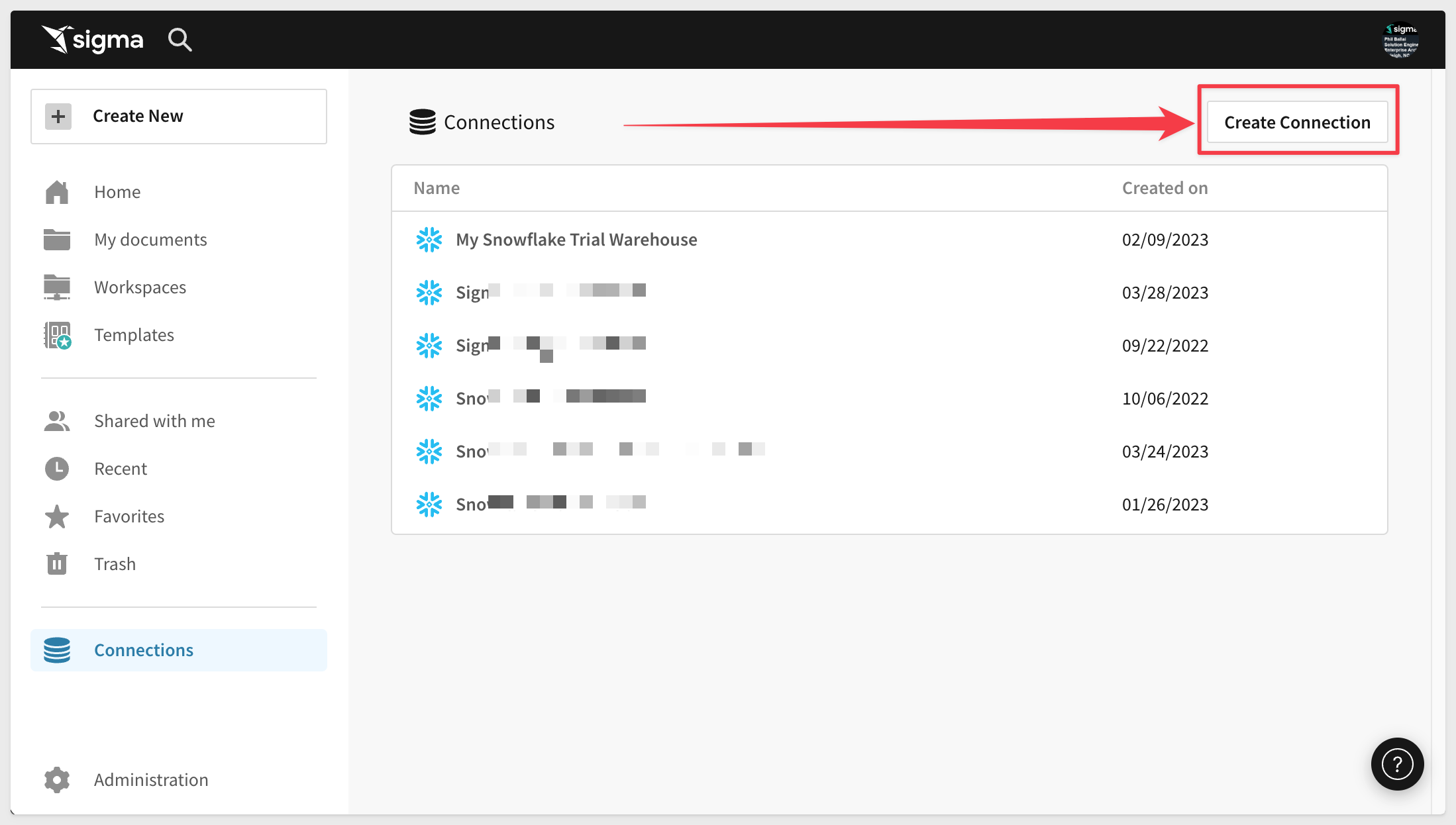
In the Account field, enter the three parts of the account URL in this format:
<account>.<region_id>.privatelink
For example, if the account URL is (as provided by Sigma):
test123.west-us-2.privatelink.snowflakecomputing.com
Then the Account field will be:
test123.west-us-2.privatelink
To complete the remaining configuration, follow the steps in the Snowflake Connection Guide
You should now be able to use the Snowflake connection (over Private Link) as you would any other connection in Sigma.

To support Private Link for Databricks we use a Front-end Private Link, also known as user to workspace. A front-end Private Link connection allows Sigma to connect to the Azure Databricks web application over a VNet interface endpoint.
Provide Databricks Resource ID to Sigma
In Azure Services, navigate to Azure Databricks:
Open the Workspace you want to connect to and click to open the JSON View:
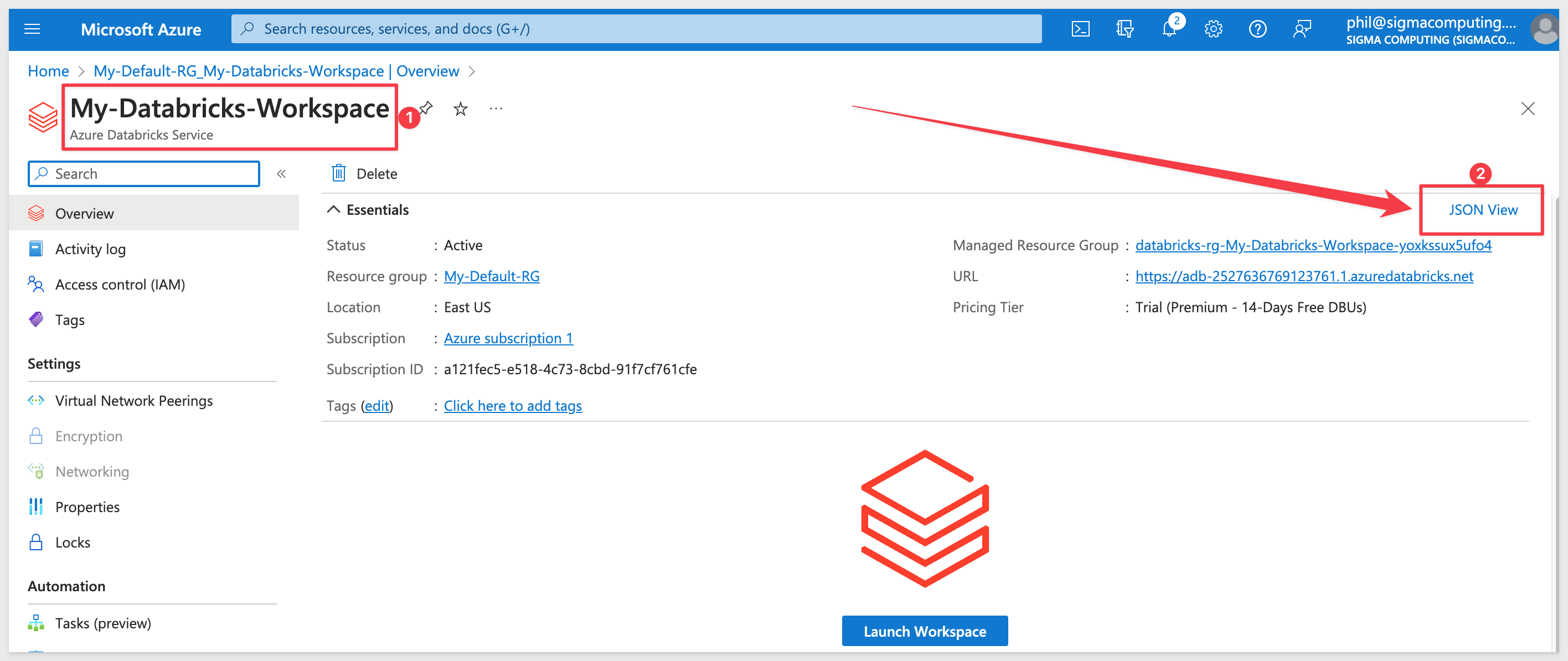
Copy the Resource ID (1). For Location (2), copy the region name for the Databricks warehouse:
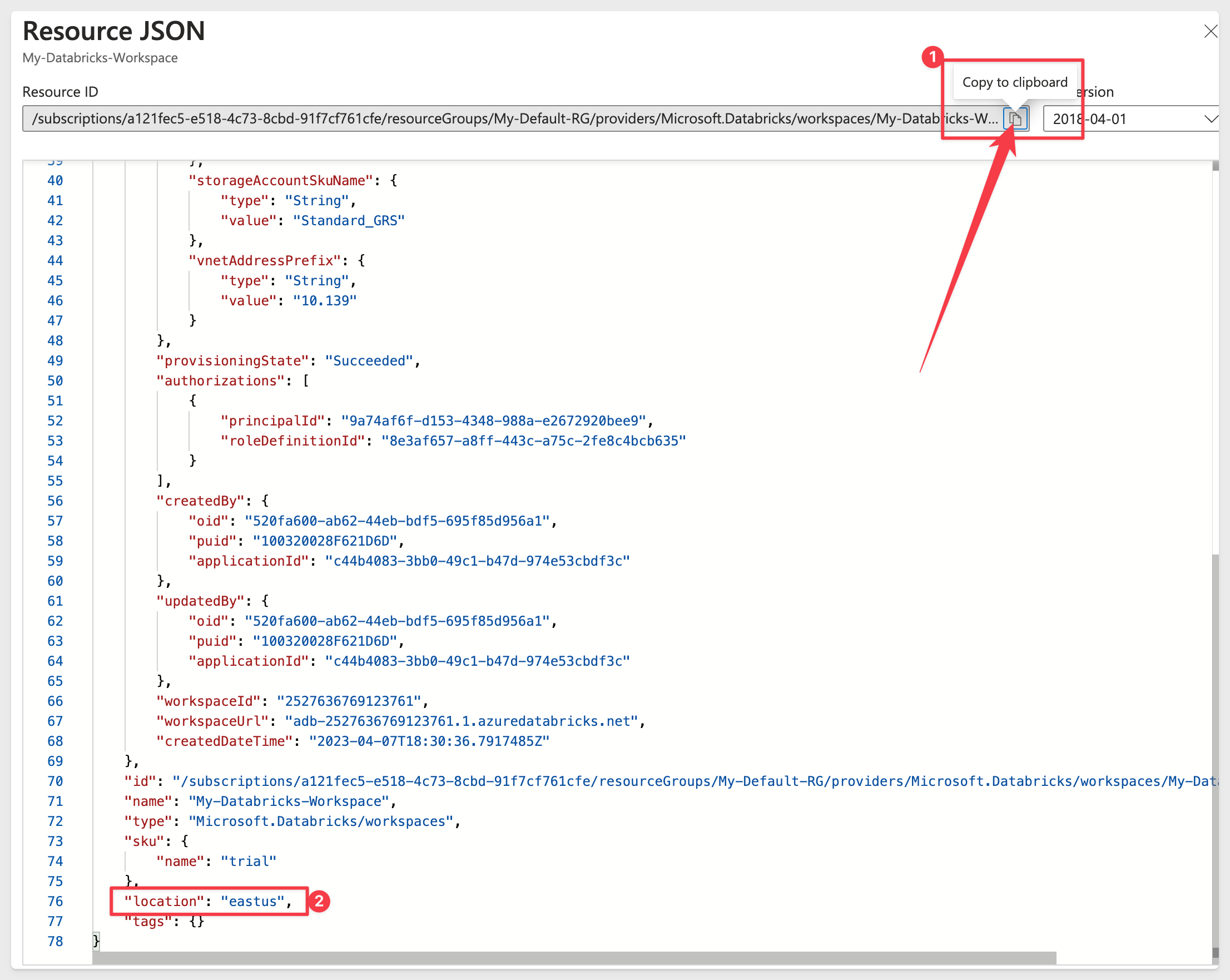
In the example above, the Resource ID is:
/subscriptions/a12xxxc5-xxxx-xxx-8cbd-91fxxf761cfe/resourceGroups/My-Default-RG/providers/Microsoft.Databricks/workspaces/My-Databricks-Workspace
and the region name is:
eastus
Copy the values generated for your Databricks account and send these to your Sigma account manager.
Sigma will create a Private Link and alert you when the link is active.
Once you receive notification from Sigma (in email) you can create the new connection in Databricks.
Configure Databricks
In the Databricks section of Azure, click on the warehouse instance > Databricks Workspace.
Click Launch Workspace:
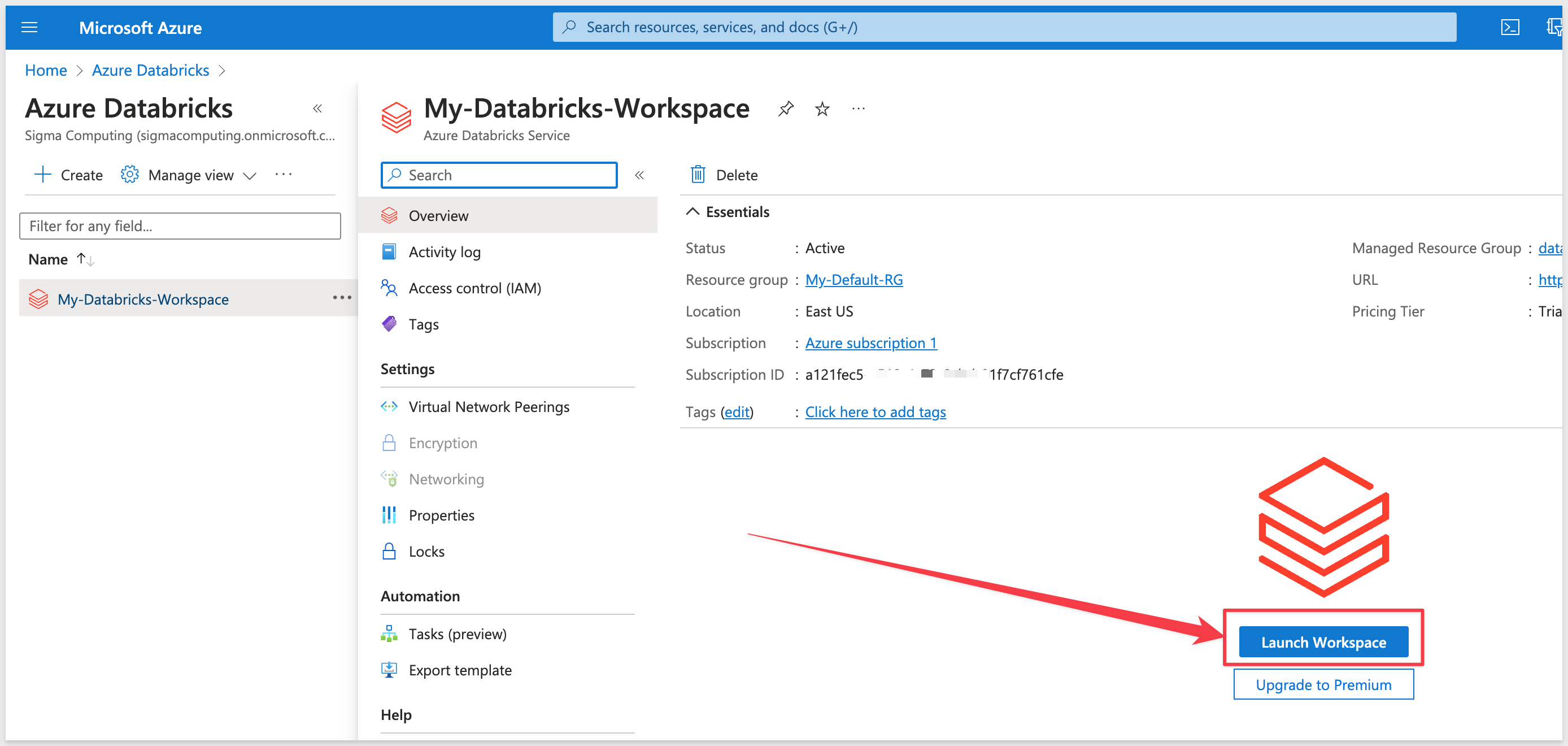
This will launch you into the Databricks console:
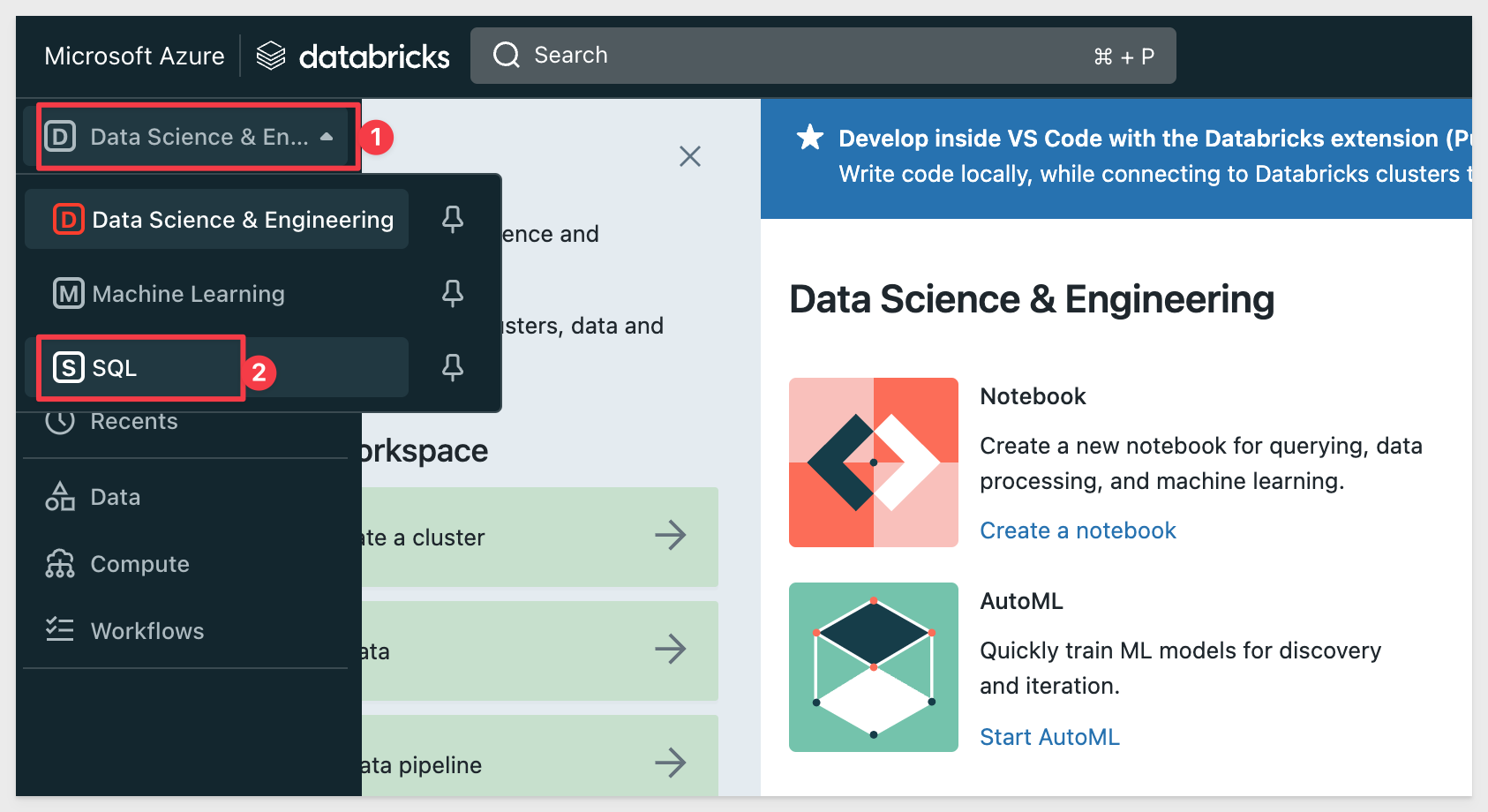
In Databricks, select the Data Science & Engineering dropdown and select SQL:
Click Review SQL Warehouses:
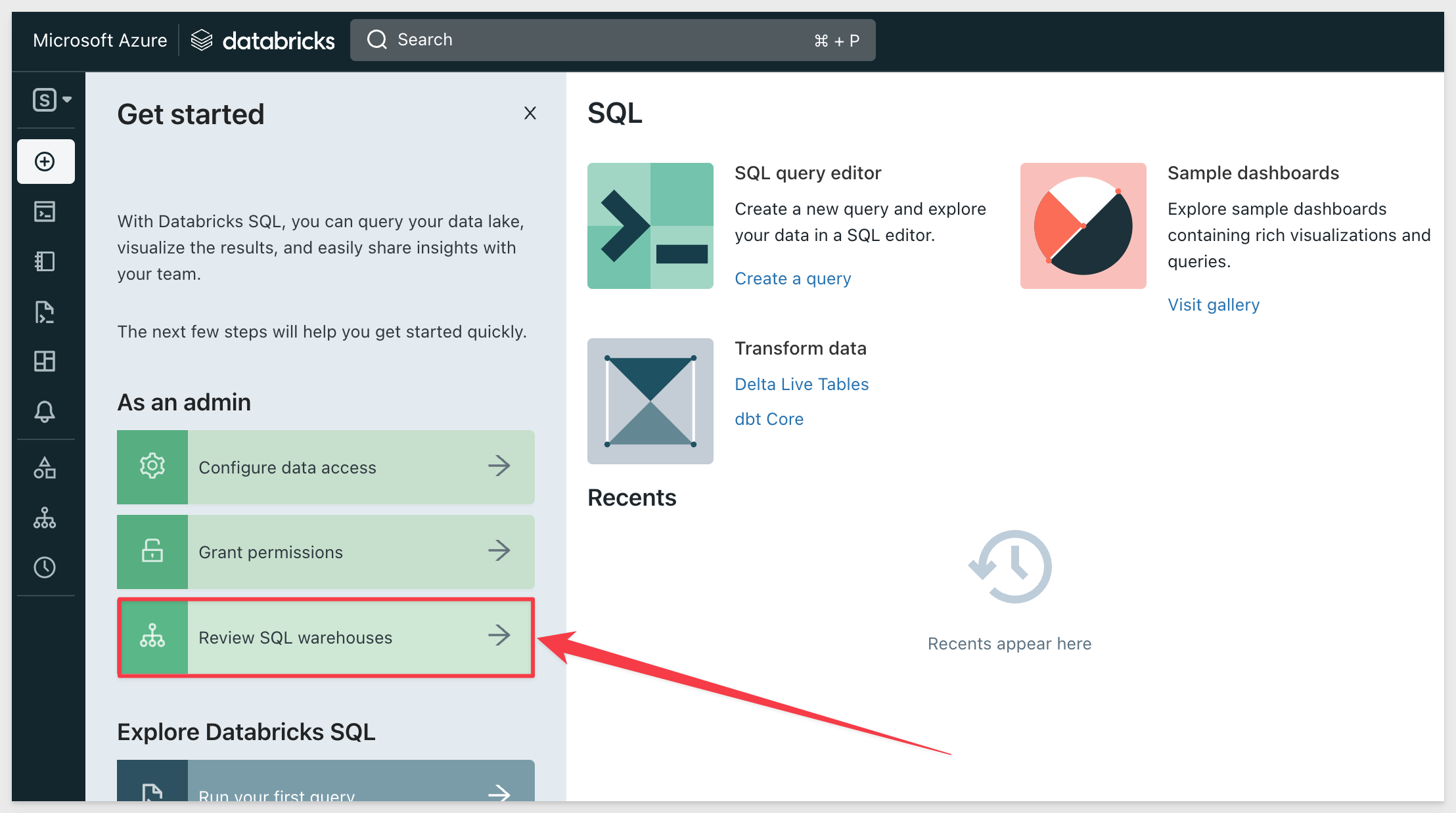
Select the warehouse you want to work with:
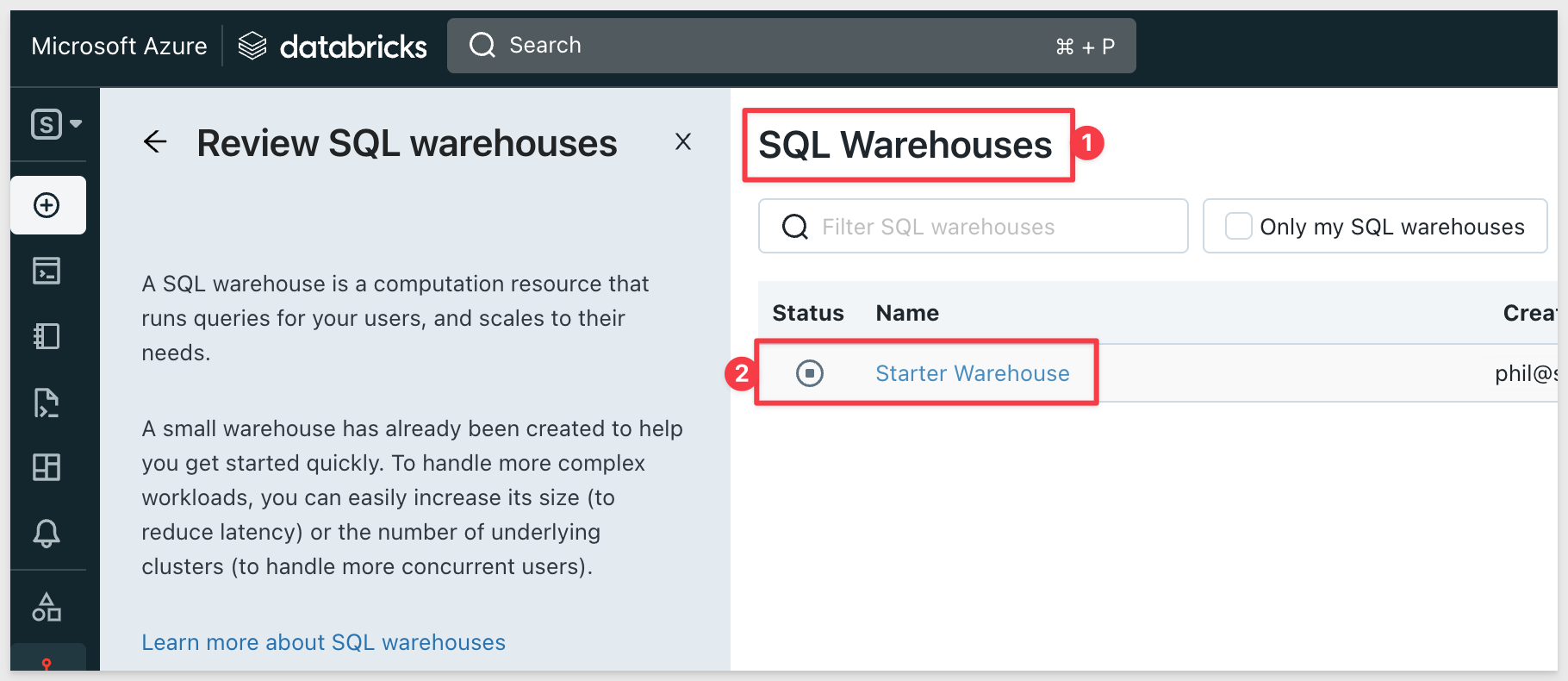
Click the Connection details tab.
Copy the Server Hostname and HTTP path values in Databricks as they are required in the Sigma UI. Save them in a text file for now.
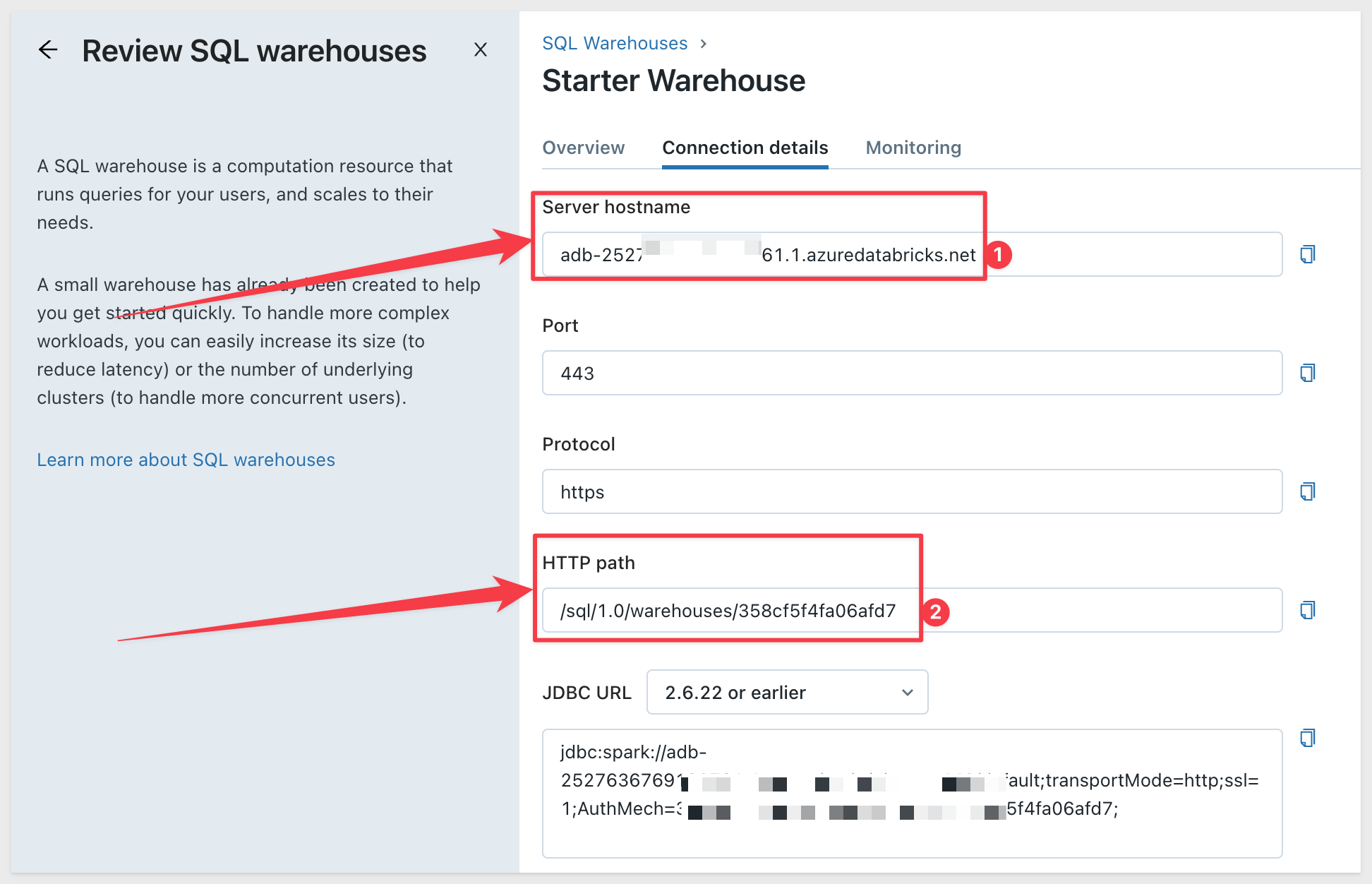
Navigate to User Settings in Databricks by clicking on your username:
Click the Personal access tokens tab and then Generate new token:
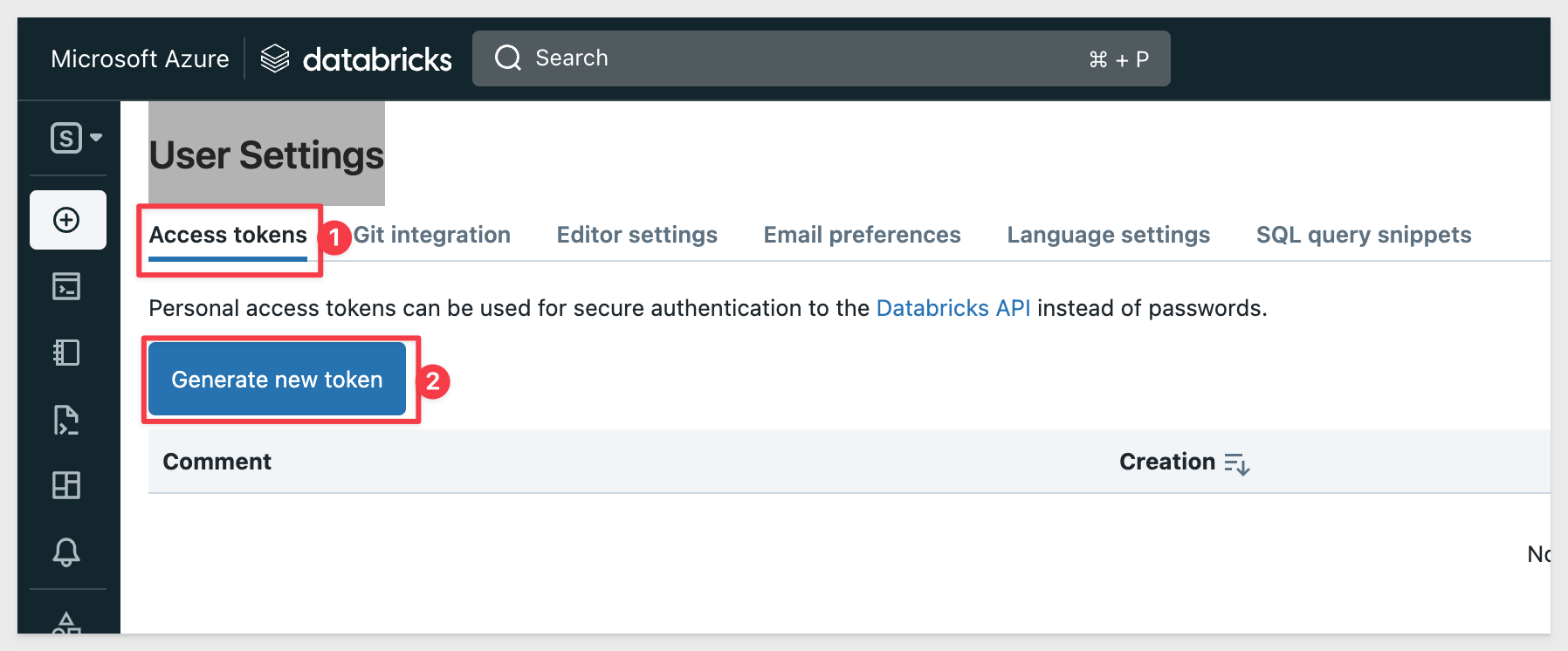
In the Lifetime field, set the token duration in days. It is a good idea to provide a comment as well.
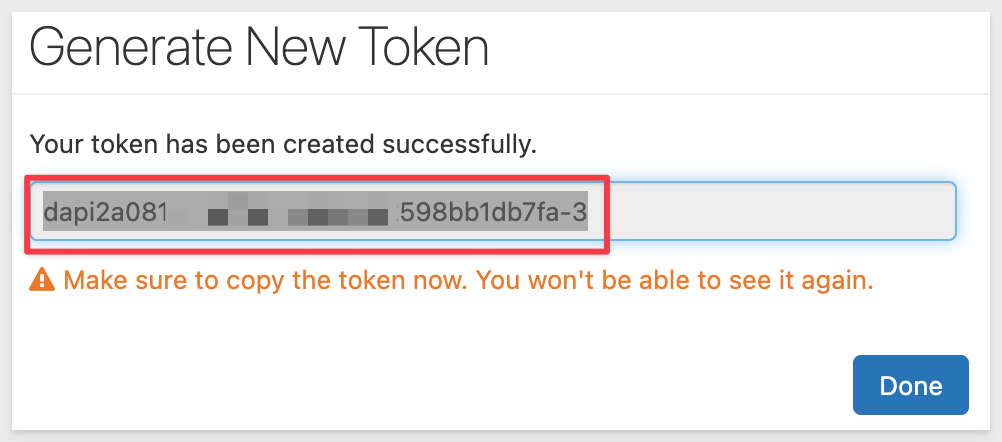
Click Generate. Copy this token as it's required in the Sigma UI. Save it in a text file for now.
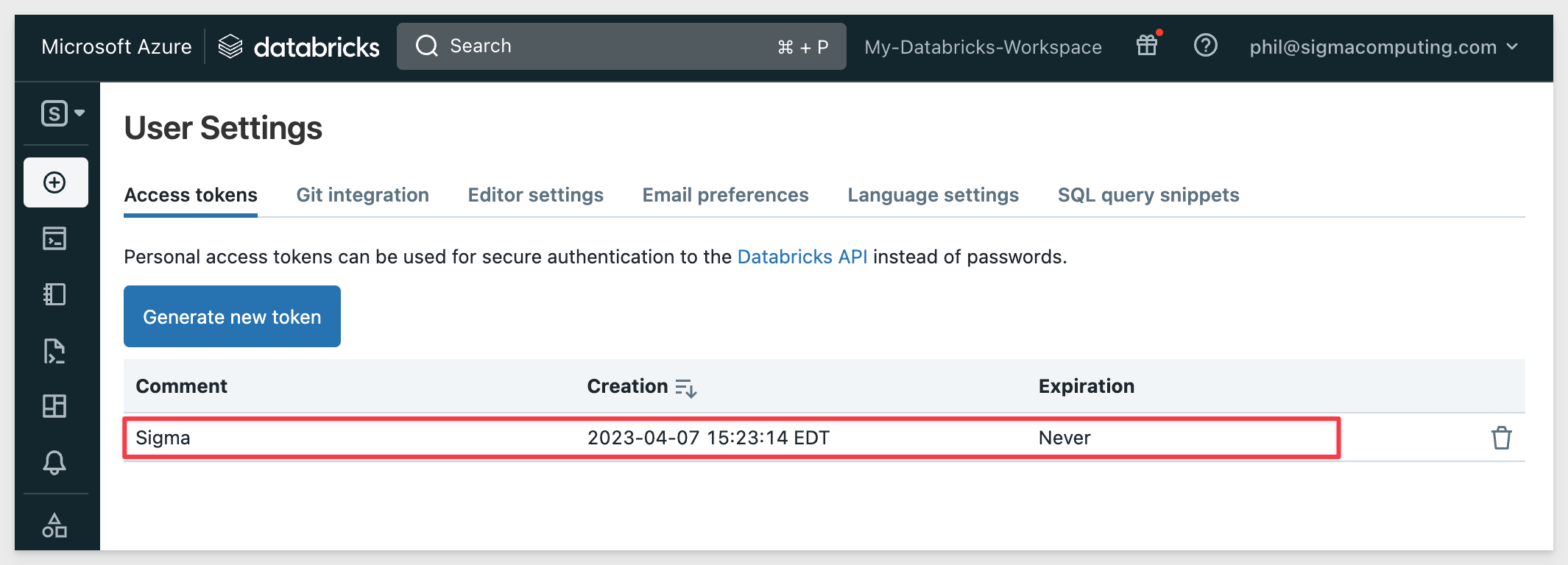
We now have a token with no expiration:
Configure Connection in Sigma
In Sigma, go to Administration > Connections > Databricks:
Click Create to create a Databricks connection.
In the Host field enter your domain name.
Paste the HTTP path value from Azure into the HTTP path field in Sigma.
Paste the token you created in Azure and enter into Access token field in Sigma.
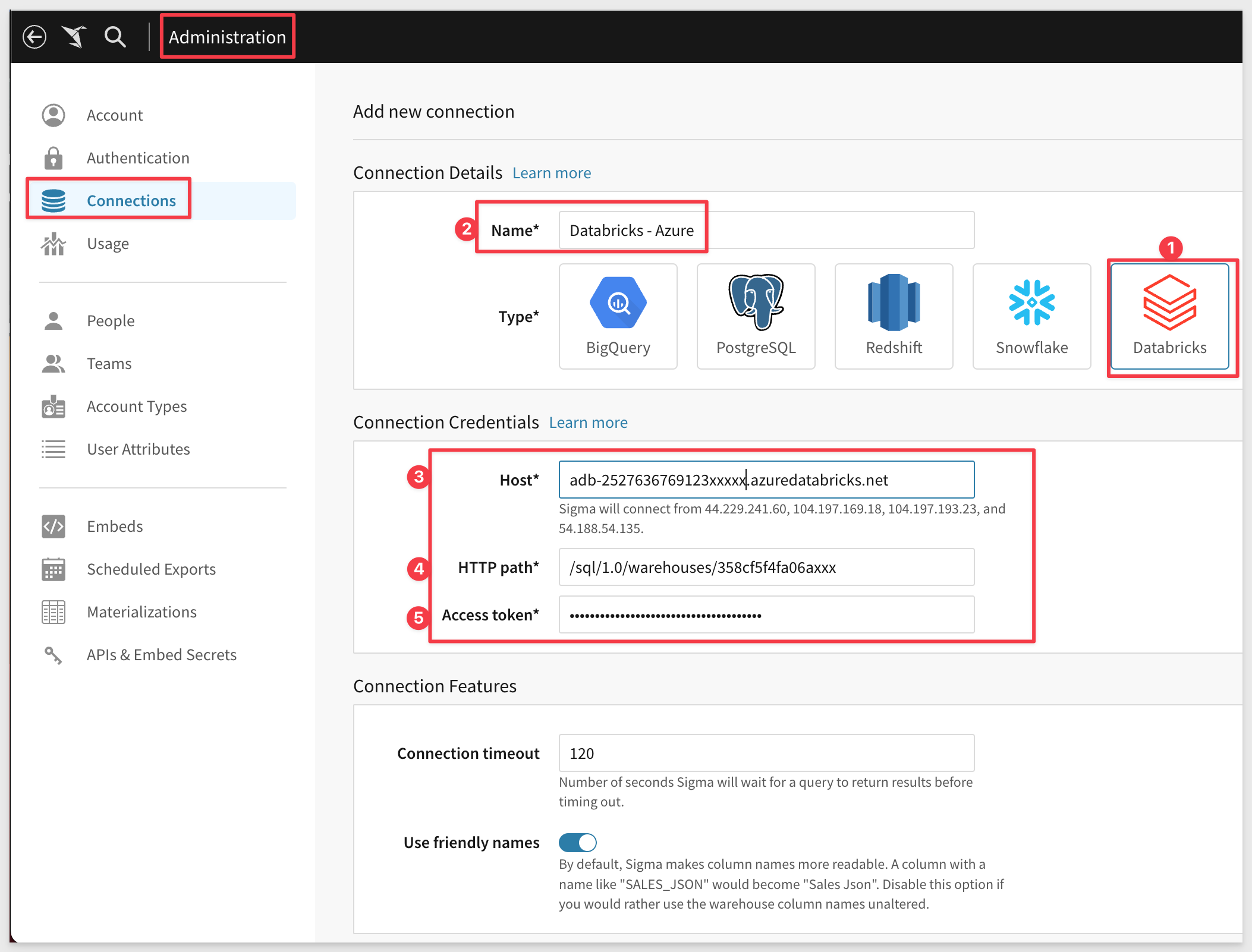
To complete the remaining configuration, follow the steps in the Databricks Connection Guide.
You should now be able to use the Databricks connection (over Private Link) as you would any other connection in Sigma.

Private Link allows you to create private endpoints for Azure Database for PostgreSQL - Single server. The private endpoint exposes a private IP within a subnet that you can use to connect to your database server just like any other resource in the VNet.
Provide PostgreSQL Info to Sigma
In the customer Azure management portal, navigate where the single server instance of PostgresSQL is. In this example, we are using Azure Database for PostgreSQL servers.
Select the instance desired for the Private Link.
Click the JSON View on the top right corner:
Copy the Resource ID (1) and Location (2):
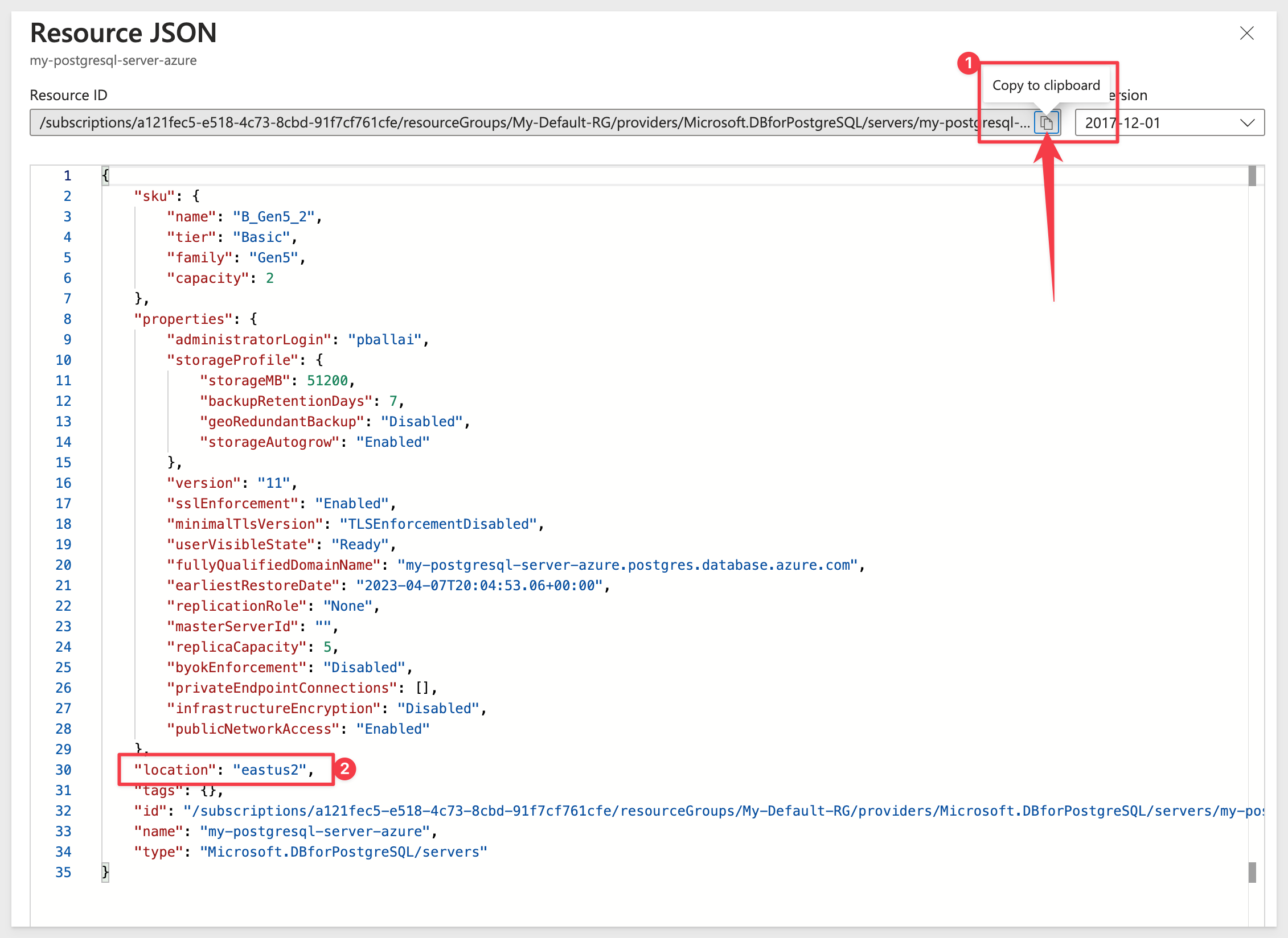
Send these two values to your Sigma account manager.
Private Link Approval
Follow the steps below to approve the Private Link after Sigma notifies you.
Click on Private endpoint connections on the left panel of the PostgreSQL server page.
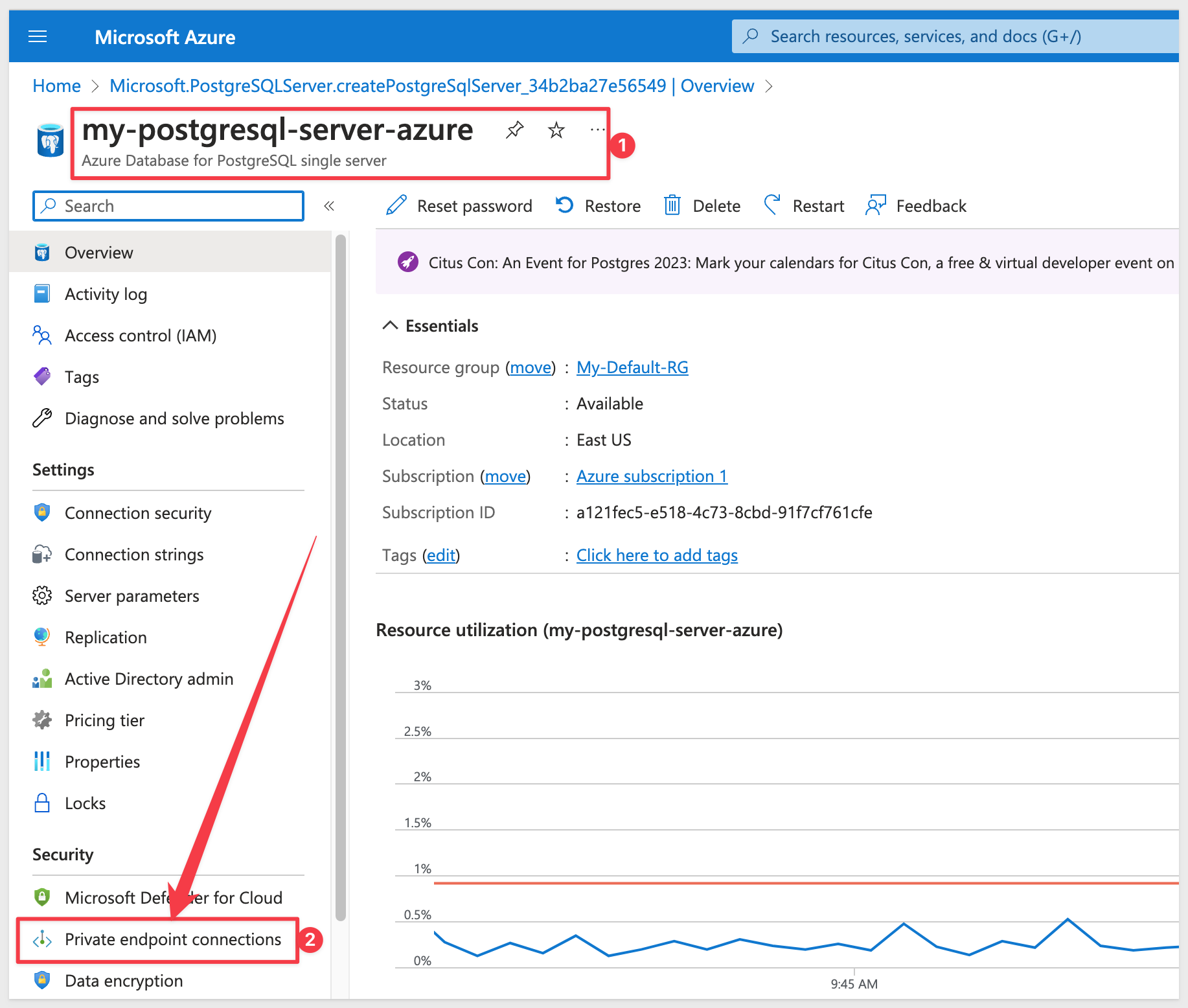
Select the recently created private endpoint connection.
The status will be Pending. Check Approve to approve the endpoint.
The private endpoint connection will change to Accepted.
Configure Sigma Connection
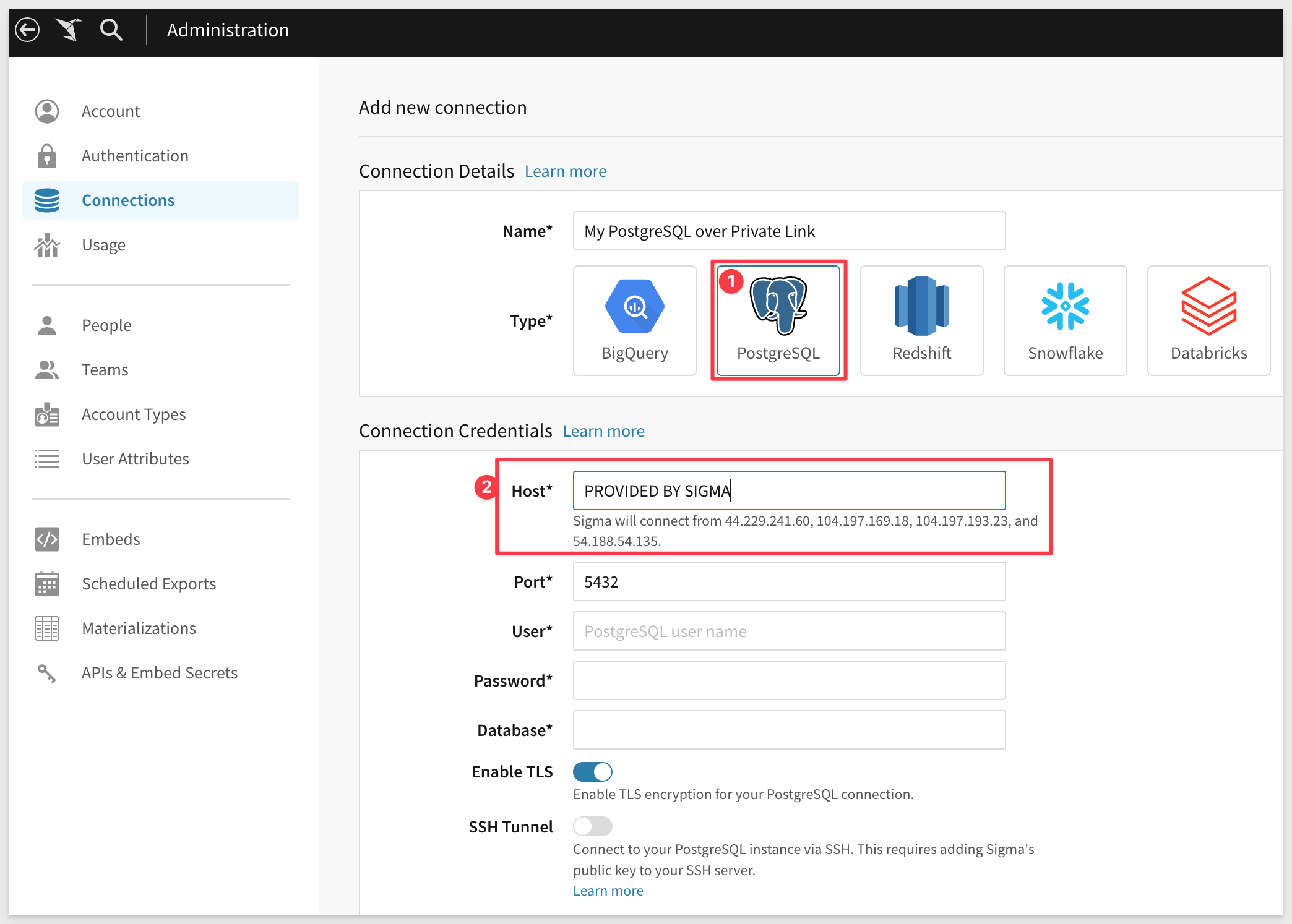
Once the Private Link has been approved, you can login to Sigma (as Administrator) and navigate to Administration > Connections.
Click to create a new connection and provide the required values.
In the Host field, enter the private endpoint Sigma provided you with in the following format:
<private_endpoint_name>.privatelink.sigma.internal
The remaining configuration is provided by the customer as usual:
The User field should be the one used to access your data warehouse.
The Password field should be the one associated with User.
The Database field should be the name of the database where your data resides.
"Enable TLS" toggle should always be checked.
"SSH Tunnel" option is not required to be toggled.
You should now be able to use the PostgresSQL connection (over Private Link) as you would any other connection in Sigma.

An overview of Private Link and how to establish an Azure Private Link connection between Sigma and data warehouse of choice.
Additional Resource Links
Be sure to check out all the latest developments at Sigma's First Friday Feature page!
Help Center Home
Sigma Community
Sigma Blog



